Computer Security - Relay Attacks
last update: 19 Nov. 2019
Introduction
Passive Keyless Entry and Start (PKES) systems is the generic name for what most people think of as the 'smart keys' of their car. Wikipedia tells us that the car key is identified via one of several antennas in a car's bodywork and through a radio pulse generator in the key housing (key-fob or card-key). The vehicle can be automatically unlocked when a sensor on the door handle is touched. The smart key can also disengage the immobiliser and activate the ignition without inserting a key, provided the key is inside the car, i.e. just press the start button with the key-fob still in your pocket. Initially the physical key and lock system on a vehicle was replaced with an electronic key providing access to the car and authorisation to drive. Later remote access was added allowing the user to open their car at a distance (this idea dates from a U.S. patent taken out in 1990). The electronic key included an immobiliser chip to prevent key copying. In 1999 the 'smart key' was introduced, where the Passive Keyless Entry and Start (PKES) system allows users to open and start their cars while having their car keys 'in their pocket'.
The PKES system usually provide three options. Firstly, using the key-fob, remotely open the car at a distance of up to 100 meters. Secondly, open and close the car (by touching the door handle) when the key-fob is within about 1 meter from the car. Thirdly, start the engine when the key-fob is inside the car. The basic idea of a relay attack is to firstly extend the distance over which the key-fob and car communicate, and secondly to intercept and retransmit the data being transmitted between the key-fob and the vehicle.
In the 1990's car manufacturers were being pushed by national authorities to introduce electronic key systems as a way to combat car theft. However as with most forms of technology, thieves looked for ways to circumvent the software. In 2011 experts were saying that with smart keys it would be impossible to steal new cars. However already in 2010 it was shown that PKES systems were vulnerable to relay attacks, a specific example of the man-in-the-middle and replay attacks.
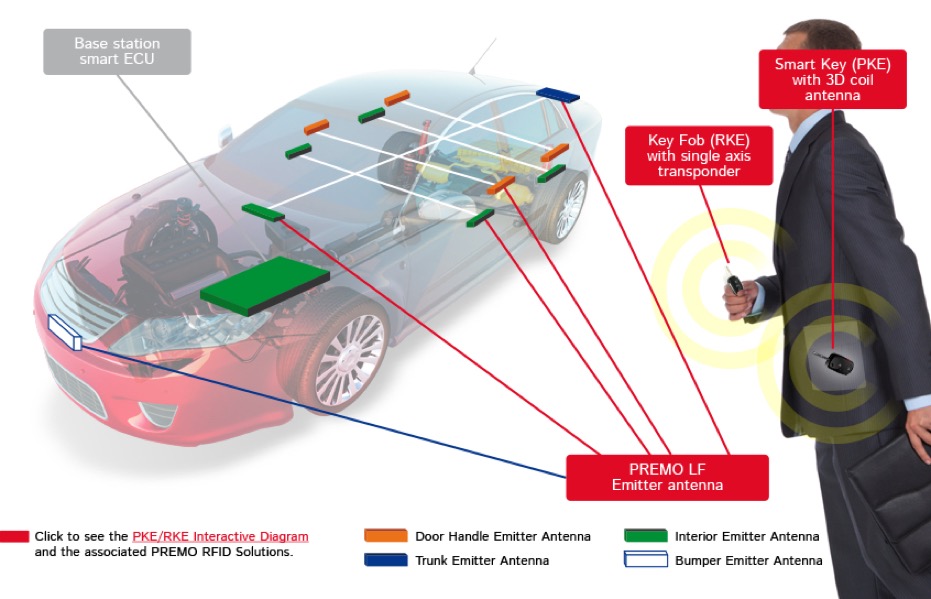
Basic Principles
PKES systems use a series of 125 kHz low-power low-frequency (LF) transmitting antennas fitted both inside and outside the vehicle (often called 'exciters'). The external antennas are usually located in the door handles, mirrors and boot (there are also 2, usually 3, or occasionally 4 'exciters' inside the vehicle). When you touch the car handle a LF signal is transmitted from the antennas to 'wake-up' the key (this is often called the 'challenge'). The key becomes activated if it is sufficiently close and it will then transmit its ID back to the vehicle via a radio frequency (RF) signal (usually 315 MHz or 434 MHz UHF). If the ID is correct the vehicle is unlocked. These systems must be quite sensitive, yet robust, and include encryption and decryption to protect the key ID.
The system does a bit more than just identify the 'owner' of the car. The 'wake-up' signal is a pre-defined string of bits which is recognised by the key-fob whilst in a very low power sleep mode (other signals or random noise can't wake-up the key-fob). The key-fob then wakes up and answers to the car controller. This whole process takes about 10 milliseconds, and the driver does not notice any delay between touching the door handle and unlocking the car. There is an anti-collision system in place to avoid interference from simultaneous key-fob signals should several key-fobs be in use. Also the key-fob receives different signal strengths from the different antennas, and I have read that it uses this to localise the key-fob. This was a quite a technical challenge since it must tell the difference between a key-fob in the pocket of a jacket on the back seat and a key-fob left in a bag on the cars sunroof. In many car user manuals they advise drivers to place the key-fob in the car in a way as to not be interpreted as being outside the vehicle (i.e. not left in door pouches or on dashboards).
The key (or transponder) is equipped with an immobiliser, a type of RFID chip embedded in the key. The car queries the RFID tag to verify if the key is authorised. The immobiliser system is designed to prevent physical copying of the key as well as any attempt to physically bypass the lock. Only a key with a previously paired RFID tag would be authorised to start the engine. RFID technology can operate both passively and actively, in PKES systems the RFID is powered by a button cell in the key.
There are at least two different ways the PKES works. Firstly, the car send out a beacon on an LF channel either periodically or when the door or boot handle is touched. Secondly, the beacon can be either a short 'wake-up' message, or a longer 'challenge' message which contains the car identifier. When woken up the key-fob computes a response and sends it on a UHF channel. The car receives the response and verifies it. The technique used to allow access to the car is different from the technique use to allow the engine to be started when the key-fob is known to be inside the car.
In routine use there are warnings concerning ways that the key-fob might not work properly. For example the signal to and from the key-fob can be significantly attenuated by a metal cover, aluminium foil, metallic boxes or wallets, coins, or even CD's and DVD's.
It is worth noting that the key-fob is a low-cost bi-directional system working at two different frequencies. The 'wake' signal sent from the car has a range of about 1 meter (max. 3 meters) whilst the key-fob is able to open and close the car at a distance anything between 10-100 meters (uni-directional push-button command of the car).
We must remember that this technology dates from 2004-2005, and thus is not what might be terms state-of-the-art. There are a number of projects that aim to replace the key-fob with a near-field communication (NFC) application. The drivers smartphone could be used in the same way as a smart key, and also provide user authentication, secure communications and e-payment services. Clearly part of the 'sales package' includes car user settings, diagnostics and car status services, and electronic immobilisation. In principle you would need to place your smartphone within 3-4 cm of the door handle to 'activate' the car.
Relay Attacks
The basics of the attack are simple. In a relay attack the attacker places one device near the key and another device near the car. The attacker then relays the message between the key and car, and can then open and start the car even if the key is physically far from the car. This can certainly work over more than 50 meters, and does not require line-of-sight. Also the key can be excited using one of the attackers devices at a distance of up to 8 meters meaning that the attacker does not need to be close to the key in order to establish the relay. The car-side device in the relay needs to be close (about 30 cm) to the car. There have been cases where the attackers activated the key-fob left on a hall table.
The cost of the relay hardware in now under $100 and systems can be purchased on the 'black market' for around $200. Check out HackRf and RollJam, which are two inexpensive and readily available tools that can be used for relay attacks. There are stories that Chinese hackers are offering a complete $20 package for relay attack hardware.
The basic premise is that communication between key and car is taken as proof of close physical proximity, i.e. the legitimate owner of the key and car has the key and is physical close to or in the car. Relay attacks get around this requirement. One type of relay attack might require to first demodulate the signal, then transmit it as a digital signal use a RF channel, and then modulate it near the victims location. The relay attack on PKES systems is easier, since it does not need to interpret or modify the signal, and is thus more or less totally transparent to an authentication or secrecy requirements in the message. In principle even a system using strong cryptography would still be vulnerable to this type of attack.
You start with a relay composed of two loop antennas connected together in a way to transmit the LF signal between the two antennas using a purpose-built RF link.

When one of the loop antennas is placed near the car door handle it captures the car beacon signal as a local magnetic field. The field excites the first antenna creating by induction an alternating signal at the output of the antenna. The signal must then be transmitted to the second antenna near the key-fob. The relayed signal creates a current in the second antenna which in turn creates a magnetic field, which in turn excites the antenna in the key-fob. The key-fob recovers the original message from the car, evaluates it, and sends the open or start engine authorisation over its UHF channel. Usually the key-fob will send an open command if the message it received is from the cars external antennas, and a start command if the message is from the cars internal antennas. So the attacked needs to actually send two signals. Firstly the attacker needs to open the car, then he must move the antenna inside the car and send a second signal to the key-fob by pushing on the 'start' engine button. In both cases the key-fob replies on a UHF channel with the appropriate authorisation (open or start).

What does a relay attack mean in practice?
Anyone can break into a car, but most modern cars have alarm systems. A thief can try to pick the lock, use a hook, or just smash the window to gain access to a vehicle.
Another technique involves the use of a simple radio jammer. As the car owner steps away from their car they use the key-fob to lock the car. If the signal is jammed by the attackers, the car will not receive the lock signal and will remain open.
Another type of attack is to eavesdrop the message from the key-fob and try to replay it back using a fake 'reader/key' pair (a so-called message-replay attack). Today most car alarm systems use an encrypted challenge-response technique which addresses this simple approach. Thieves adapted their approach. The key-fob and car have now a system called 'rolling codes'. The jammer blocks and reads the first attempt to lock the car. The owner usually presses again the key-fob to lock the car. Again the signal is jammed, but then the signal from the first jamming is sent to close the car. The owner is happy, and the thief has recorded the new 'rolling code' which he can then use to unlock the car. You can buy a so-called RollJam for $30-$40 and it has been shown to work for a range of mid-priced cars from Nissan through to Volkswagen.
One way to use the relay attack system is to have the hardware in a small briefcase and to place it very near (less than 1 meter) from the key-fob (it could be in the drivers jacket pocket). The key-fob receives the wake-up signal, 'thinks' that it is in the vicinity of the car and sends out the unlock/engine start signal. This signal is also picked up and recorded in the briefcase package. The briefcase then becomes a kind of second key, and when near the car its signal will unlock it, and when inside the car will permit an engine 'start'. An alternative is to relay the recorded signal from the key-fob to an accomplice near the car, who will then re-transmit the unlock/engine start signal and ride off with the car.
Here is a warning issued by the Staffordshire police in the U.K. concerning relay theft. Theft using this technique probably dates back to around 2011, but recently a relay theft was caught on video.
There are other more complex and even less well known types of attacks. In 2011 at a Black Hat conference security consultants demonstrate that they could send commands from a laptop and unlock and start a car using a sms message over the in-car gsm phone system. Once they had obtained the number of the in-car system they were able to masquerade as an authorised server.
Reference
Most of the information on this webpage comes from a variety of source, but check out the summary of Anna Richardson in "Security of Vehicle Key Fobs and Immobilisers".
"Comprehensive Experimental analyses of Automotive Attack Surfaces" is a more extensive analysis of how modern cars are vulnerable to attack.